Moovapps Process
Creating External Data Connections of Type OpenID in Process {#process_openid}
To configure the two external data connections, you will need information provided by the client, specifically:
- The Azure AD tenant ID
- The application ID created by the client in Azure AD
- The value of the secret of the application created by the client in Azure AD
Authentication Delegation for Process
This configuration is only required if the Process instance does not use Team
Place the following configuration in Administration -> Server -> Configuration -> Properties -> Settings tab:
# Azure
oidc.issuer.url=https://login.microsoftonline.com/<Azure AD tenant ID>/v2.0
oidc.client.id=Azure AD application ID (tenant)
oidc.client.secret=Azure AD secret value (delegation application)
oidc.redirect.url=https://<domain name>/<webapp>/navigation/openid-connect-redirect
oidc.postlogout.url=https://<domain name>
oidc.scope=openid profile
oidc.login.claim.parameter.name=preferred_username
oidc.metadata.url=https://login.microsoftonline.com/<tenant ID>/v2.0/.well-known/openid-configuration
com.axemble.security.ExternalAuthenticationAction.allowedAddresses=<ip ou domaine autorisé>
# ------------------------------------------------------------------------
# Prevent redirection for anonymous process creation button
# (set to true if some users come from the Process directory and not Azure AD)
# ------------------------------------------------------------------------
workplace.automatic.redirection.to.team.authentication.page=false
Starting from v2025.1, your configuration is automatically migrated to an OpenID U2M external data connection. If your configuration lines are not automatically removed, it means some information is missing in your external data connection configuration. The missing configuration line will be: oidc.issuer.url=https://login.microsoftonline.com//v2.0 Add it and make sure the configuration lines disappear when saved. Your connection will then be correctly configured.
User Sync for ETL
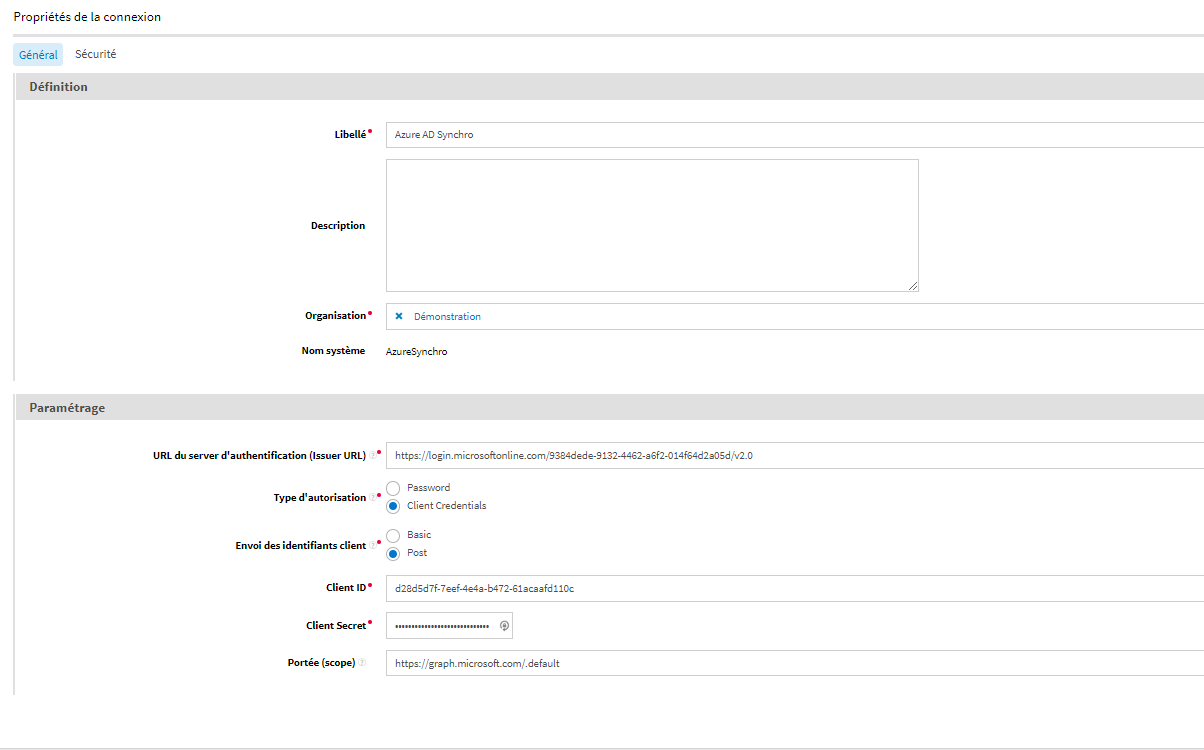
In Process administration, create a new external data connection and fill in the appropriate information, including:
-
the URL of the authentication server with the Azure AD tenant ID
https://login.microsoftonline.com/<Azure AD tenant ID>/v2.0
-
the client ID (which is the Azure AD application ID)
-
the client secret (which is the Azure AD secret value)
-
OpenID scopes: https://graph.microsoft.com/.default
Moovapps ETL Configuration {#etl_config}
To configure ETL for user and/or group synchronization, follow the procedure:
Import the Azure Starter Pack for your ETL version, downloadable from the documentation in the Resources Center
The pack is not present in the ETL 4.5.0 folder, for this version use the v4.4.2 pack.
Azure AD User Synchronization
Declare an ETL agent:
<configuration>
<variables>
<!-- Connection variables -->
<variable name="azure-tenant-id"></variable>
<variable name="azure-openid-connection-name"></variable>
<variable name="azure-query-params">$expand=memberOf</variable>
<variable name="parent-organization-uri"></variable>
<variable name="authentication-domain-name"></variable>
<variable name="synchronizeUsersGroupsLinks">false</variable>
<variable name="azureQueryFilterGroupId"></variable>
<variable name="azureQuerySelect">id,userPrincipalName,givenName,surname,mail,preferredLanguage,businessPhones,mobilePhone,accountEnabled,country,memberOf,jobTitle,manager,officeLocation,department,state</variable>
<variable name="enable-deletion">false</variable>
<variable name="force-deletion">false</variable>
<variable name="keep-local-groups">true</variable>
</variables>
<!-- Synchronization route selection -->
<extend name="route-azure-users" />
</configuration>
Adapt the agent configuration to your environment:
| Parameter | Expected Value |
|---|---|
| azure-tenant-id | Azure AD tenant ID |
| azure-openid-connection-name | Name of the external connection declared earlier |
| azure-query-params | allows retrieval of user-associated groups |
| parent-organization-uri | parent organization, e.g.: uril://vdoc/organization/Collaborators |
| authentication-domain-name | Name of the Team delegation to associate with AzureAD |
| synchronizeUsersGroupsLinks | allows synchronization of links with pre-synchronized groups |
| azureQueryFilterGroupId | AzureAD group ID if filtering by group |
| azureQuerySelect | list of user fields to retrieve in the query; add if you want to customize the query, otherwise do not declare in the agent |
| enable-deletion | allows disabling users already synchronized but no longer present in the sync |
| force-deletion | by default, deletion is limited to 100 users per sync; this parameter removes that limitation |
| keep-local-groups | allows keeping local Process groups (otherwise they are deleted) starting from v2024 |
The enable-deletion option is only functional starting from v4.4.1 of Visiativ ETL. If you use an older version, do not use this option.
To enable the enable-deletion option on an instance where sync was already in place, you must first deactivate all previously synchronized user accounts via an export/import, for example. Only then can you execute the route with the parameter set to true.
A problem exists in v4.4.1 with this option. The cache used by enable-deletion is unique to a route. So, if you configure 2 agents with the same route, a conflict occurs and each agent deletes users from the other agent. You must therefore duplicate the route for each agent (fixed starting from v4.4.2).
For more information on configuring the ETL route, refer to the Moovapps ETL documentation in the functional documentation of Moovapps ETL available in Resources Center.
The Azure ETL Pack also available in Resources Center provides an import template for synchronization.
Azure AD Group Synchronization
Azure AD group synchronization manages group creation and associations with subgroups.
The first execution may fail if subgroups haven’t yet been synchronized in Process. A second ETL route execution may be needed to properly synchronize and associate all groups.
Declare an ETL agent:
<configuration>
<variables>
<!-- Connection variables -->
<variable name="azure-tenant-id"></variable>
<variable name="azure-openid-connection-name"></variable>
<variable name="parent-organization-uri"></variable>
<variable name="azure-query-params">$expand=memberOf</variable>
<variable name="keep-local-groups">true</variable>
</variables>
<!-- Synchronization route selection -->
<extend name="route-azure-groups" />
</configuration>
Adapt the agent configuration to your environment:
| Parameter | Expected Value |
|---|---|
| azure-tenant-id | Azure AD tenant ID |
| azure-openid-connection-name | Name of the external connection declared earlier |
| azure-query-params | allows retrieval of user-associated groups |
| parent-organization-uri | parent organization, e.g.: uril://vdoc/organization/Collaborators |
| keep-local-groups | allows keeping local Process groups from v2024 onwards using the latest ETL version compatible with your Process version |
For more information on configuring the ETL route, refer to the Moovapps ETL documentation in the functional documentation of Moovapps ETL available in Resources Center.
The Azure ETL Pack also available in Resources Center provides an import template for synchronization.
Best Practices for Configuring the Azure AD ETL Driver
-
The route is pre-configured to populate a custom ADDomain attribute with the value
AzureAD(This setting is only useful if you use Visiativ Team)AzureADis the default domain name for internal organization users, so it’s best to use this value- Use a suffix matching the organization name for external organizations (e.g., “AzureAD-Client1”)
-
The user and group sync routes share Azure AD connection parameters
- It is therefore possible to create a single ETL agent for both routes by declaring the Azure AD connection parameters only once:
<configuration>
<variables>
<!-- Connection variables -->
<variable name="azure-tenant-id"></variable>
<variable name="azure-openid-connection-name"></variable>
<variable name="azure-query-params">$expand=memberOf</variable>
<variable name="parent-organization-uri"></variable>
<variable name="authentication-domain-name"></variable>
<variable name="synchronizeUsersGroupsLinks">false</variable>
<variable name="azureQueryFilterGroupId"></variable>
<variable name="azureQuerySelect">id,userPrincipalName,givenName,surname,mail,preferredLanguage,businessPhones,mobilePhone,accountEnabled,country,memberOf,jobTitle,manager,officeLocation,department,state</variable>
<variable name="enable-deletion">false</variable>
<variable name="force-deletion">false</variable>
<variable name="keep-local-groups">true</variable>
</variables>
<!-- Synchronization route selection -->
<extend name="route-azure-users" />
<extend name="route-azure-groups" />
</configuration>
Testing Federation
User Sync Test
-
Verify that a user is correctly synchronized after ETL execution (creation and update)
- In the Process directory
- In the Team directory (if used)
-
If the synchronizeUsersGroupsLinks parameter is true, verify users are properly linked to their groups
-
If the enable-deletion parameter is true, verify that deactivated users are indeed disabled in the Process directory
-
Try logging in with an Azure AD synchronized user
-
Try logging in with a “Process” user (not created by ETL sync)
Group Sync Test
-
Verify that a group is correctly synchronized after ETL execution (creation and update)
- In the Process directory
-
Verify that subgroups are correctly associated with their parent groups